It seems you can hardly go a day without hearing about another data breach, money transfer scam, or some other crime that started out as a spear phishing attack. Email-borne threats have always been a top priority for IT security, but spear phishing is one of the fastest growing attacks. This threat evolves and changes, and when done correctly, will blend in with a victim's legitimate communications. This is because spear phishing has a human touch. Attackers spend time crafting strategies, researching targets, and refining their methods until they are successful or have made a decision to move on.
When you really dig into spear phishing attacks, you find there are a few specific reasons why they work so well. In this blog post, we will take a look at the top three reasons why criminals are so successful with these attacks.
You think you have an account with them
Attackers do not want you to know who they really are, so they spoof email domains to look like a trusted brand. About 53% of these attacks spoof Microsoft and Apple, with the rest of the attacks spoofing names like UPS, Chase, and Amazon. Attackers design email templates to impersonate the brand, which makes it more likely that readers will fall for the scam. The content of the email messages may be warnings of a security breach or some other request that prompts the recipient to click on a link to confirm account login credentials or verify identity.
The links in these messages may appear legitimate, but actually take the victim to a phishing website that is being used to steal login credentials. If the attacker can capture your login credentials, he can then access other resources in your name or potentially use your account to launch more attacks within your company. In fact, one of the reasons why Microsoft is one of the brands used most often in these attacks is that Office 365 credentials are often a gateway into an organization. If attackers are able to capture this set of credentials, they may be able to login to the network and launch further attacks.
You think you work for them
If you aren't familiar with the Business Email Compromise (BEC) attack, you certainly aren't alone. These scams are only 6% of spear-phishing attacks, but they cost a lot to organizations. The FBI states that financial losses from BEC attacks since 2013 currently stand at over $12.5 billion. And more will go unreported and uncounted in law enforcement statistics.
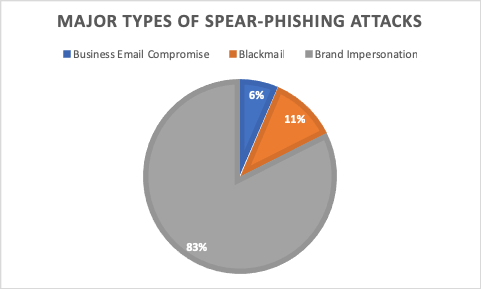
Why are the costs so high for a scam that represents only 6% of spear phishing? BEC attack emails are designed to look like someone you can trust; your boss, a corporate executive, or a member of another department who may have legitimate authority to make a request. These scams usually request payment on an invoice, a transfer of money, or some confidential and sensitive data. The amount of money lost in an invoice or transfer scam can be huge, as demonstrated by the attacks on Facebook and Google. The two tech giants sent about $100 million to the banks of the attackers. Losses from BEC data breaches can result in response costs and regulatory fees of tens to hundreds of thousands.
You think they can embarrass you
1 in 10 spear-phishing attacks is the new ‘sextortion' scam, which is an attempt to blackmail a victim by claiming ownership of a compromising video. The attacker often starts with an email address and password combination that was stolen in a data breach at some point prior to the attack. These credentials are harvested from collections on the dark web and then used as evidence to demonstrate that the attacker has private information about the victim. Once the attacker has established ‘credibility’ by using credentials stolen in an old data breach, he will then make his demands. Usually, this involves some private video, images, or web browsing information. The criminal has no such content, but if you don't want to risk it, then you might meet his demands.
Protect yourself
Spear phishing works so well because traditional email security is only partially effective on these attacks. Email security gateways are an important line of defense, but spear phishing is sometimes able to slip through these gateways and attack the humans.
- Attacks are carefully designed and targeted, sometimes after months of research on the intended victim. They are built to look like a and they are not sent in bulk.
- Email services like Gmail are often used to launch the attacks, which means the sending domain has a high-reputation score and aren't likely to be stopped based on sending domain.
- In the absence of obviously malicious links or attachments, as in the case of the BEC attack, there may be no traditional indicators that an email message is an attack.
Spear Phishing: Top Threats and Trends is a free report that details all of these attacks, including how they work and why traditional security isn't enough. The report is based on Barracuda research and includes examples of attacks, top brands impersonated, commonly used subject lines, and more. Best practices and recommended training and technology are included as well.
Download the free report here.
Over 200,000 businesses use Barracuda's solutions to protect against cybersecurity threats. Run a free scan to get a comprehensive report of your cybersecurity risk profile.









